In this article, we will look at how to enable the Transport Layer Security (TLS 1.2) protocol on different Windows versions, including cases for .Net and WinHTTP applications. TLS 1.0 and TLS 1.1 are deprecated protocol versions. If you have migrated all your services to TLS 1.2 or TLS 1.3, you may disable support for legacy TLS versions on your Windows servers and clients (How to Disable TLS 1.0 and TLS 1.1 Using GPO). However, prior to doing it, make sure that all your clients support TLS 1.2.
In modern Windows versions (Windows 11/10/8.1 or Windows Server 2022/2019/2016/2012R2), TLS 1.2 is enabled by default. In previous Windows versions (Windows 7, Windows Server 2008R2/2012), you will have to configure some settings before you can enable TLS 1.2.
Windows XP and Vista do not support TLS 1.2.
For example, in order to enable TLS 1.2 in Windows 7 and Windows Server 2008 R2:
- Make sure that Windows 7 Service Pack 1 is installed;
- Download and manually install the MSU update KB3140245 from Microsoft Update Catalog (https://www.catalog.update.microsoft.com/search.aspx?q=kb3140245);

- Then download and install the MicrosoftEasyFix51044.msi (the patch adds the registry options allow to enable TLS 1.2 support on Windows 7/2008R2/2012);
Without these updates, Outlook on Windows 7 will fail to connect to a modern e-mail server with an error: 0x800CCC1A – Your server does not support the connection encryption type you have specified. In addition, if you open some websites, you may see an SSL error This site can’t provide a secure connection.
- Restart your computer.
These registry options are described in the article Update to enable TLS 1.1 and TLS 1.2 as default secure protocols in WinHTTP in Windows (https://support.microsoft.com/en-us/topic/update-to-enable-tls-1-1-and-tls-1-2-as-default-secure-protocols-in-winhttp-in-windows-c4bd73d2-31d7-761e-0178-11268bb10392).
The following REG_DWORD registry items will appear on your computer in HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\ and HKLM\...Protocols\TLS 1.2\Servers:
- DisabledByDefault = 0
- Enabled = 1
In order to use TLS 1.2 by default for WinHttp API apps, add the DefaultSecureProtocols = 0x00000A00 REG_DWORD parameter to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp (on Windows x64: HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp).
Here are the possible values of DefaultSecureProtocols option which defines allowed protocols for WinHTTP connections:
- 0x00000A0 – a default value allowing SSL 3.0 and TLS 1.0 for WinHTTP only
- 0x0000AA0 — allows using TLS 1.1 and TLS 1.2 in addition to SSL 3.0 and TLS 1.0
- 0x00000A00 – allows TLS 1.1 and TLS 1.2 only
- 0x00000800 – allows TLS 1.2 only
Starting with Windows 10 and Windows Server 2016, all Windows versions support TLS 1.2 for WinHTTP.
You may use the following PowerShell script to create these registry parameters:
$reg32bWinHttp = "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp"
$reg64bWinHttp = "HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp"
$regWinHttpDefault = "DefaultSecureProtocols"
$regWinHttpValue = "0x00000800"
$regTLS12Client = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
$regTLS12Server = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"
$regTLSDefault = "DisabledByDefault"
$regTLSValue = "0x00000000"
$regTLSEnabled = "Enabled"
$regTLSEnableValue = "0x00000001"
# for Windows x86
New-ItemProperty -Path $reg32bWinHttp -Name $regWinHttpDefault -Value $regWinHttpValue -PropertyType DWORD
# for Windows x64
New-ItemProperty -Path $reg64bWinHttp -Name $regWinHttpDefault -Value $regWinHttpValue -PropertyType DWORD
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2”
New-Item -Path $regTLS12Client
New-Item -Path $regTLS12Server
New-ItemProperty -Path $regTLS12Client -Name $regTLSDefault -Value $regTLSValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Client -Name $regTLSEnabled -Value $regTLSEnableValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Server -Name $regTLSDefault -Value $regTLSValue -PropertyType DWORD
New-ItemProperty -Path $regTLS12Server -Name $regTLSEnabled -Value $regTLSEnableValue -PropertyType DWORD
Restart your computer using the command:

Then you have to enable TLS 1.2 support for .NET Framework apps. To do this, you need to enable the system encryption protocols for .NET 3.5 and 4.x apps in the registry. If you are using old NET Framework versions, like 4.5.1 or 4.5.2 on Windows Server 2012 R2/2012 or Windows 8.1, first install the latest updates for .Net Framework 4.5.1 (they will add TLS 1.2 support for .NET).
Find the registry option to be configured for different .Net versions below:
for .Net 3.5 or 2.0:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727]"SystemDefaultTlsVersions"=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727]"SystemDefaultTlsVersions"=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727]"SchUseStrongCrypto"=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727]"SchUseStrongCrypto"=dword:00000001
for .Net 4.х:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]"SystemDefaultTlsVersions"=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319]"SystemDefaultTlsVersions"=dword:00000001
for .Net 4.6:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]"SchUseStrongCrypto"=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319]"SchUseStrongCrypto"=dword:00000001
For example, without these options, you won’t be able to connect to PSGallery repositories from your PowerShell console on Windows Server 2012 R2 with the following errors:
The problem is that by default PowerShell tries to use TLS 1.0 to connect to PSGallery. As of April 2020, the PowerShell Gallery only accepts TLS 1.2 connections.
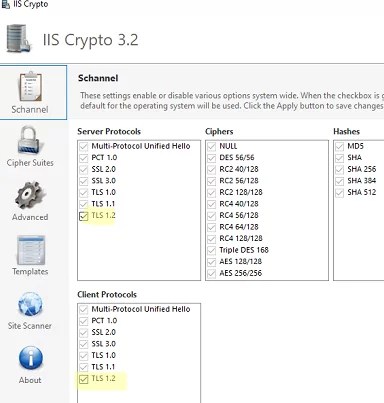
Also, there is a free IISCrypto tool, that allows to enable/disable various TLS/SSL versions and Schannel settings through a GUI (https://www.nartac.com/Products/IISCrypto/). Here you may select what TLS versions you want to enable. If all checkboxes next to Schannel protocols are inactive (gray out), Windows is using the default settings. In my example, I have enabled TLS 1.2 for a server and a client using the PowerShell script shown above. IISCrypto is now showing that TLS 1.2 was enabled manually.
IISCrypto doesn’t allow changing TLS settings for .NET or WinHTTP.
On Windows Server 2022, TLS 1.3 must be enabled to support HTTP/3 for IIS websites.
As an expert in the field of cybersecurity and Windows system administration, I have extensive experience in configuring and securing Transport Layer Security (TLS) protocols on various Windows versions. My expertise is grounded in practical implementation, troubleshooting, and staying abreast of the latest developments in secure communication protocols.
The article you provided discusses the process of enabling the Transport Layer Security (TLS 1.2) protocol on different Windows versions, with a focus on .Net and WinHTTP applications. I will break down the key concepts discussed in the article:
-
TLS Protocol Versions:
- TLS 1.0 and TLS 1.1 are deprecated, and the article emphasizes the need to migrate to TLS 1.2 or TLS 1.3.
- The importance of disabling support for legacy TLS versions using Group Policy Objects (GPO) is highlighted.
-
Default TLS 1.2 Support:
- Modern Windows versions (Windows 11/10/8.1 or Windows Server 2022/2019/2016/2012R2) have TLS 1.2 enabled by default.
- For older versions like Windows 7 and Windows Server 2008R2/2012, specific settings need to be configured before enabling TLS 1.2.
-
Enabling TLS 1.2 on Windows 7 and Server 2008R2:
- Ensure Windows 7 Service Pack 1 is installed.
- Manually install the MSU update KB3140245 from the Microsoft Update Catalog.
- Install MicrosoftEasyFix51044.msi to add registry options enabling TLS 1.2 support.
-
Registry Configuration:
- Registry settings are added under
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\andHKLM\...Protocols\TLS 1.2\ServerswithDisabledByDefaultandEnabledDWORD values.
- Registry settings are added under
-
WinHttp Configuration:
- Default secure protocols for WinHTTP connections are controlled through the
DefaultSecureProtocolsregistry parameter. - PowerShell script provided for creating the necessary registry parameters.
- Default secure protocols for WinHTTP connections are controlled through the
-
.NET Framework Support:
- Enable system encryption protocols for .NET 3.5 and 4.x apps in the registry.
- Different registry options for different .NET versions, such as
SystemDefaultTlsVersionsandSchUseStrongCrypto.
-
IISCrypto Tool:
- The IISCrypto tool is introduced as a free tool to enable/disable various TLS/SSL versions and Schannel settings through a GUI.
- It allows selecting TLS versions to enable/disable.
-
TLS 1.3 and Windows Server 2022:
- Mention of the need to enable TLS 1.3 for supporting HTTP/3 on IIS websites in Windows Server 2022.
In conclusion, the article provides a comprehensive guide for configuring and enabling TLS 1.2 on different Windows versions, covering aspects related to registry settings, WinHTTP, .NET Framework, and the IISCrypto tool. The information is valuable for system administrators and security professionals aiming to enhance the security of their Windows environments.
