Which is better IKEv1 or IKEv2?
IKEv2 is better than IKEv1. IKEv2 supports more features and is faster and more secure than IKEv1. IKEv2 uses leading encryption algorithms and high-end ciphers such as AES and ChaCha20, making it more secure than IKEv1. Its support for NAT-T and MOBIKE also makes it faster and more reliable than its predecessor.
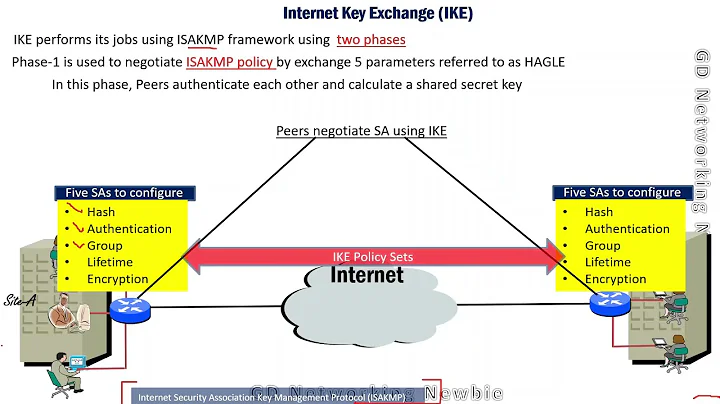
ISAKMP is a generic key management and security association creation protocol for use in TCP/IP networks. IKE is an implementation of ISAKMP used for IPSEC key management.
IKEv2 provides the following benefits over IKEv1: In IKEv2 Tunnel endpoints exchange fewer messages to establish a tunnel. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode).
IKEv1 phase 1 negotiation aims to establish the IKE SA. This process supports the main mode and aggressive mode. Main mode uses six ISAKMP messages to establish the IKE SA, but aggressive mode uses only three. Therefore, aggressive mode is faster in IKE SA establishment.
Fusion Embedded IKEv2 Features
Legacy IKEv1 support, including support for ISAKMP (RFC 2408), IKE (RFC 2409), the Internet DOI (RFC 2407), NAT traversal, legacy authentication, and remote address acquisition.
The researchers found that IKEv1 is vulnerable to Bleichenbacher oracle attacks, a cryptographic attack technique that has been known for almost two decades. A Bleichenbacher attack involves sending modified ciphertext to a device and obtaining information about its unencrypted value based on the device's response.
IKE or Internet Key Exchange protocol is a protocol that sets up Security Associations (SAs) in the IPSec protocol suite. And, ISAKMP or Internet Security Association and Key Management Protocol is a protocol that is used to establish SA and cryptographic keys.
Deprecating IKEv1
IKEv1 is deprecated and MUST NOT be deployed. Systems running IKEv1 should be upgraded and reconfigured to run IKEv2. Systems that support IKEv1 but not IKEv2 are most likely also unsuitable candidates for continued operation.
The ISAKMP protocol is a framework for dynamically establishing security associations and cryptographic keys in an Internet environment. This framework defines a set of message flows (exchanges) and message formats (payloads). ISAKMP defines a generic payload for key exchange information.
In IKEv2 Tunnel endpoints exchange fewer messages to establish a tunnel. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication.
Does IKEv2 use aggressive mode?
The ikev2 protocol has nothing to do with aggressive mode or main mode at all. If you do a "sh crypto isa" it will show you the ikev1 sa and the ikev2 sa.
IKEv2 Phases
Like IKEv1, IKEv2 also has a two-phase negotiation process to create a secure tunnel. The first phase of IKEv2 is IKE_SA_INIT and the second phase of IKEv2 is IKE_AUTH.
Quick mode exchange messages. In Quick mode, each message contains an encrypted hash. This hash authenticates the source of the message (for example, verifies that it is bound to an ISAKMP SA), authenticates the integrity of the message, and proves liveliness.
While Aggressive Mode is faster than Main Mode, it is less secure because it reveals the unencrypted authentication hash (the PSK). Aggressive Mode is used more often because Main Mode has the added complexity of requiring clients connecting to the VPN to have static IP addresses or to have certificates installed.
The Internet Security Association and Key Management Protocol (ISAKMP) and IPSec are essential to building and encrypting VPN tunnels. ISAKMP, also called IKE (Internet Key Exchange), is the negotiation protocol that allows hosts to agree on how to build an IPSec security association.
In IKEv2 Tunnel endpoints exchange fewer messages to establish a tunnel. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication.
Deprecating IKEv1
IKEv1 is deprecated and MUST NOT be deployed. Systems running IKEv1 should be upgraded and reconfigured to run IKEv2. Systems that support IKEv1 but not IKEv2 are most likely also unsuitable candidates for continued operation.
Internet Key Exchange (also known as IKE, IKEv1 or IKEv2) is a protocol that is used to generate a security association within the Internet Protocol Security protocol suite.
IKE is a part of IPsec, a suite of protocols and algorithms used to secure sensitive data transmitted across a network. The Internet Engineering Task Force (IETF) developed IPsec to provide security through authentication and encryption of IP network packets and secure VPNs.