FAQs
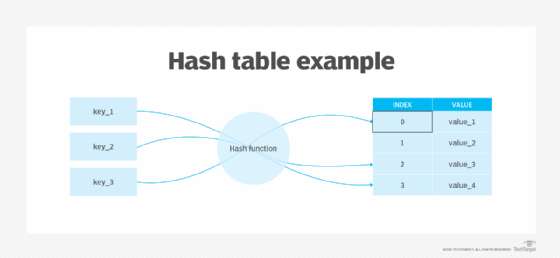
Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables.
What is hashing explain with an example? ›
Hashing is an important data structure designed to solve the problem of efficiently finding and storing data in an array. For example, if you have a list of 20000 numbers, and you have given a number to search in that list- you will scan each number in the list until you find a match.
What is a hashing function correct answer? ›
Definition: A hash function is a function that takes a set of inputs of any arbitrary size and fits them into a table or other data structure that contains fixed-size elements.
What is hashing simple? ›
Hashing is simply passing some data through a formula that produces a result, called a hash. That hash is usually a string of characters and the hashes generated by a formula are always the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces 32 character-long hashes.
What is a real example of hashing? ›
Real-World Example of Hashing: Online Passwords
Every time you attempt to log in to your email account, your email provider hashes the password YOU enter and compares this hash to the hash it has saved. Only when the two hashes match are you authorized to access your email.
How does hashing protect data? ›
Data is mapped to an output of fixed size using hash functions, referred to as hashing. It is employed to confirm the integrity of files containing data. In the case of encryption, the message is encrypted so that only those users with the proper authorization can read it.
What is a good example of hash function? ›
Hash functions (hashing algorithms) used in computer cryptography are known as "cryptographic hash functions". Examples of such functions are SHA-256 and SHA3-256, which transform arbitrary input to 256-bit output.
What are 5 examples of hashing algorithms? ›
Hashing algorithms are just as abundant as encryption algorithms, but there are a few that are used more often than others. Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN. MD5: This is the fifth version of the Message Digest algorithm.
Where are hashing used? ›
Hashing is a function used to map data to a fixed-length value. Businesses use hashing in authentication systems and to validate different types of data, such as files and documents. Understanding what hashing is and how it's used is important because it can help to prevent data breaches and protect stored information.
Why is hashing important? ›
What are the benefits of Hashing? One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
You can use hashing functions to speed up the retrieval of data records (simple one-way lookups), to validate data (by using checksums), and to perform cryptography.
What are the three hashing functions? ›
Types of Hash functions
- Division Method.
- Mid Square Method.
- Folding Method.
- Multiplication Method.
The most commonly used method for hashing is known as modular hashing, which involves mapping a key k into one of the m slots by taking the remainder of k divided by m. This can be represented by the hash function h(k) = k mod m. For example, if the hash table has size m = 12 and the key is k = 100, then h(k) = 4.
How many keys does hashing require? ›
The basic operation of hash functions does not need any key and operate in a one-way manner. The one-way operation means that it is impossible to compute the input from a particular output. The basic uses of hash functions are: Generation and verification of digital signatures.
What is the purpose of hashing in a database? ›
Hashing is an effective technique to calculate the direct location of a data record on the disk without using index structure. Hashing uses hash functions with search keys as parameters to generate the address of a data record.
Is hashing one-way? ›
While there are many types of two-way encryption, hash functions are one-way encryption, which makes them even tougher codes to crack.
Is hashing the same as encryption? ›
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Is hashing still used? ›
SHA-2 hash code family is widely used today, with algorithms that are longer and harder to break. The names of SHA-2 algorithms are connected to length, so SHA-224 represents 224 bits in length. The same format works for SHA-256, SHA-384 and SHA-512.
Do hackers use hashing? ›
For example, a hacker could use a dictionary attack to run popular and predictable passwords through commonly used hashing algorithms, and see if the hashed result is in their leaked database.
How is hashing more secure? ›
Hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value). Hashing is appropriate for password validation. Even if an attacker obtains the hashed password, they cannot enter it into an application's password field and log in as the victim.
Applications of Hashing Algorithms
- Verifying the integrity of messages and files. An important application of secure hashes is the verification of message integrity. ...
- Signature generation and verification. ...
- Password verification. ...
- Proof-of-work. ...
- File or data identifier.
To the time of writing, SHA-256 is still the most secure hashing algorithm out there. It has never been reverse engineered and is used by many software organizations and institutions, including the U.S. government, to protect sensitive information.
Which algorithm is best for hashing? ›
SHA-256: This hashing algorithm is a variant of the SHA2 hashing algorithm, recommended and approved by the National Institute of Standards and Technology (NIST). It generates a 256-bit hash value. Even if it's 30% slower than the previous algorithms, it's more complicated, thus, it's more secure.
Can you Unhash a hash? ›
You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.
Does hashing use a key? ›
A hash function takes a key as an input, which is associated with a datum or record and used to identify it to the data storage and retrieval application. The keys may be fixed length, like an integer, or variable length, like a name. In some cases, the key is the datum itself.
Why is hashing better than encryption? ›
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
What are the problems in hashing? ›
List of coding problems using hashing
- Minimum deletions to make all elements same using hash table.
- Maximum distance between two occurrences of same element in array.
- Check if two arrays are similar or not using hashing.
- Minimum number of operations to make all elements same using hashing.
Components of Hashing: Hash Table: An array that stores pointers to records that correspond to a specific phone number. If no existing phone number has a hash function value equal to the index for the entry, the entry in the hash table is NIL.
Why is hashing irreversible? ›
Pre-Image Resistance — The idea here is that a strong hash algorithm is one that's preimage resistance, meaning that it's infeasible to reverse a hash value to recover the original input plaintext message. Hence, the concept of hashes being irreversible, one-way functions.
What are five key properties of a hashing function? ›
The Characteristics of Cryptographic Hash Functions
- It accepts a message of any length.
- It produces a fixed-length message digest.
- It is easy (and therefore fast) to compute the message digest for any given message.
- The hash is irreversible – it is not possible to generate a message from its message digest.
In particular, cryptographic hash functions exhibit these three properties: They are “collision-free.” This means that no two input hashes should map to the same output hash. They can be hidden. It should be difficult to guess the input value for a hash function from its output.
What does a hash key look like? ›
Also called a hash, number sign, or pound sign, the octothorpe is the typographical symbol "#" (two horizontal lines and two vertical lines, crossed). On US QWERTY keyboards, the # symbol appears on the same key as the number 3.
What is the standard for hashing? ›
The Secure Hash Standard specifies five secure hash algorithms, SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512.
What is the difference between hash and public key? ›
In hashing, keys are not used but keys are used to encrypt information in encryption. Only public keys are used for symmetric encryption. Both public and private keys are utilised in asymmetric encryption.
What is hashing a password? ›
Hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, cybercriminals don't get access to your password. Instead, they just get access to the encrypted “hash” created by your password.
What is the point of hashing? ›
Hashing helps to both encrypt and decrypt digital signatures, which are mathematical algorithms used to routinely validate the authenticity and integrity of a digital document or message. Hash functions transform the digital signature before the hash value, and the signature gets sent to the receiver.
What is the difference between hashing and encryption? ›
Encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication.
Is hashing better than encryption? ›
Since encryption is two-way, the data can be decrypted so it is readable again. Hashing, on the other hand, is one-way, meaning the plaintext is scrambled into a unique digest, through the use of a salt, that cannot be decrypted.
Why is hashing used Crypto? ›
Hashing in cryptocurrencies
Hashing is an integral part of all blockchain-based transactions, including the trading of cryptocurrency. Hash functions are necessary in everything from mining blocks to signing transactions to generating private keys. A hash function is a mathematical algorithm used to calculate the hash.
Does hashing require a key? ›
The basic operation of hash functions does not need any key and operate in a one-way manner. The one-way operation means that it is impossible to compute the input from a particular output. The basic uses of hash functions are: Generation and verification of digital signatures.
Hashing is almost always preferable to encryption when storing passwords inside databases because in the event of a compromise attackers won't get access to the plaintext passwords and there's no reason for the website to ever know the user's plaintext password.
Why is hashing a one-way function? ›
Put simply, a hash function scrambles data to encrypt it, making it unreadable without special keys or difficult hacking techniques. While there are many types of two-way encryption, hash functions are one-way encryption, which makes them even tougher codes to crack.
What is hashing not good for? ›
Hashing is not good for applications where multiple records with the same key value are permitted. Hashing is not a good method for answering range searches. In other words, we cannot easily find all records (if any) whose key values fall within a certain range.
What is the strongest hashing method? ›
SHA-256 is one of the hashing algorithms that's part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It's the most widely used and best hashing algorithm, often in conjunction with digital signatures, for: Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
Can hashing be reversed? ›
You can't reverse hashing functions: they are not a form of encryption. That's why hashes are always the same length regardless of the input length: they throw away information in order to generate a (hopefully) unique value from the input.
Does Bitcoin use hashing? ›
Bitcoin uses the SHA-256 hash algorithm. This algorithm generates verifiably random numbers in a way that requires a predictable amount of computer processing power.
How long is a hash in a blockchain? ›
Blockchain Hash Function. A hash function takes an input string (numbers, alphabets, media files) of any length and transforms it into a fixed length. The fixed bit length can vary (like 32-bit or 64-bit or 128-bit or 256-bit) depending on the hash function which is being used. The fixed-length output is called a hash.
How many bits is a Bitcoin hash? ›
In particular, the Bitcoin hash algorithm is SHA-256 or Secure Hashing Algorithm 256 bits.