When I got my first YubiKey, I plugged it into my laptop, tried setting it up with a few accounts, then gave up. For a year and a half. It doesn't matter how computer-literate you are, or how much you value security—something about the YubiKey just feels confusing. But it doesn't have to.
The YubiKey is a device that makes two-factor authentication as simple as possible. Instead of a code being texted to you, or generated by an app on your phone, you press a button on your YubiKey. That's it. Each device has a unique code built on to it, which is used to generate codes that help confirm your identity. Press the button and you can log in.
We could get into the math, and break down the various protocols supported by devices like this, but most users don't need to know any more than "enter your username and password, as usual, then press the button on the YubiKey to log in."
A YubiKey is required to access many of Zapier's internal tools, so I've finally gotten around to learning how to use one. I'm glad I did—here's why, and how you can set one up too.
YubiKey isn't the only hardware two-factor authentication device on the market—just the most popular. There are a number of similar devices out there, and most of the information outlined in this article applies to them.
What is two-factor authentication?
We've written extensively about two-factor authentication, but it's necessary to go over the basics before we can explain why hardware two-factor authentication devices are a good idea.
Passwords are terrible. Most are too easy for hackers to guess, and the rest are too long or complicated for humans to remember. Even secure passwords are useless once they've been leaked, and leaks are basically inevitable. For these reasons, and more, it's a good idea not to rely entirely on passwords. That's the entire idea behind two-factor authentication (often shortened to 2FA).
With two-factor authentication, you need two things to sign in: your password, yes, but also something else that proves you are who you say you are. You're probably familiar with two ways of doing 2FA:
SMS or email codes. Apps send you a code, which you need to enter before you can log in. This is the easiest method to set up because you don't need to install any software or purchase any hardware. It's also the least secure because email and SMS are both unencrypted and easily compromised.
Authentication apps. Apps you want to log in to will ask you for a code that you can retrieve by opening an app on your phone, like Google Authenticator or Authy. This is far more secure than relying on SMS or email, but it's not exactly convenient—you need to grab your phone, open an app, then type out a code.
The YubiKey represents a third way of doing two-factor authentication: hardware authentication. Apps ask you to plug a tool like a YubiKey into your device and press a button. The YubiKey sends a unique code that the service can use to confirm your identity. This is more secure, because the codes are much longer, and more convenient, because you don't have to type out the codes yourself.
There's a lot more nuance than this, of course. But for the most part, you just need to know that it's 2FA that's more secure and easier to use.
Why is a YubiKey better than other 2FA?
We've gone over this a little, but let's talk about why a YubiKey (and similar devices) is better than other forms of 2FA. To name a few:
Convenience. SMS, email, and authentication apps all require that you copy and paste, or manually enter, a code. With the YubiKey, you just press a button on a device attached to your computer.
Much longer codes. Other 2FA methods typically only send you a six-digit code to confirm your identity, basically because it would be unreasonable to expect humans to type much more than that. YubiKeys don't ask you to manually type a code, so they're free to use much longer codes. That's more secure.
Easy to migrate. Did you get a new computer? Just unplug your YubiKey from the old one, plug it into the new one, and you can log in to all of your apps, same as before. You can also use one key to log in to your account on multiple computers. I've found the process to be much easier than migrating other 2FA.
Really hard to hack. It's relatively easy for hackers to compromise your email or SMS. It's a lot harder—close to impossible with current technology—to fake the codes generated by a unique hardware device.
Again, there's a lot more nuance here, but these are the broad advantages of the YubiKey over other forms of 2FA.
How to set up your YubiKey
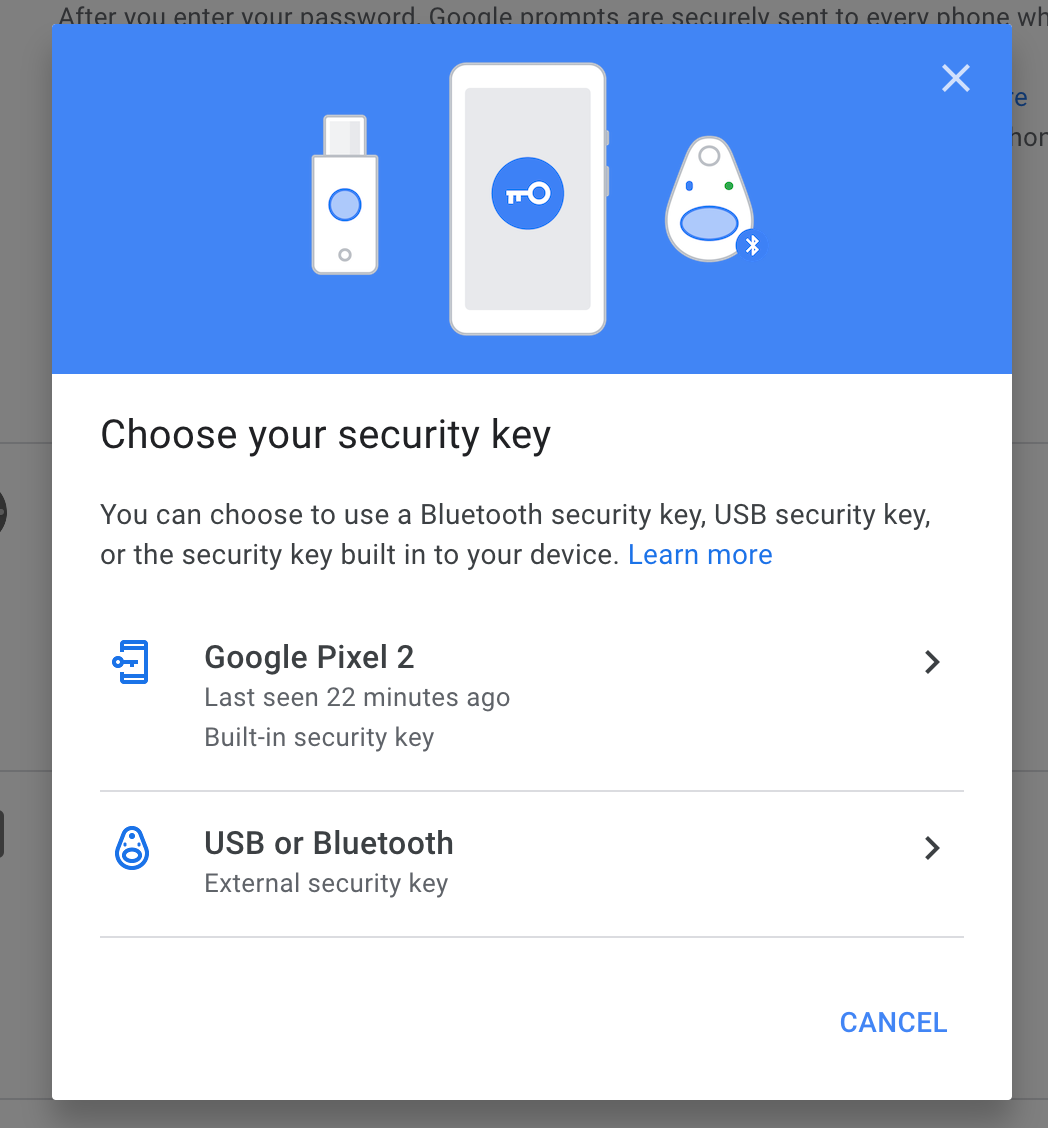
Setting up your YubiKey isn't that different from setting up app-based two-factor authentication. If you're actually using a YubiKey (not another hardware authenticator), here's what you need to do:
Plug in your YubiKey.
Head to Yubico.com/setup and click your device.
Browse the list of supported apps and find what you want to secure.
Follow the instructions.
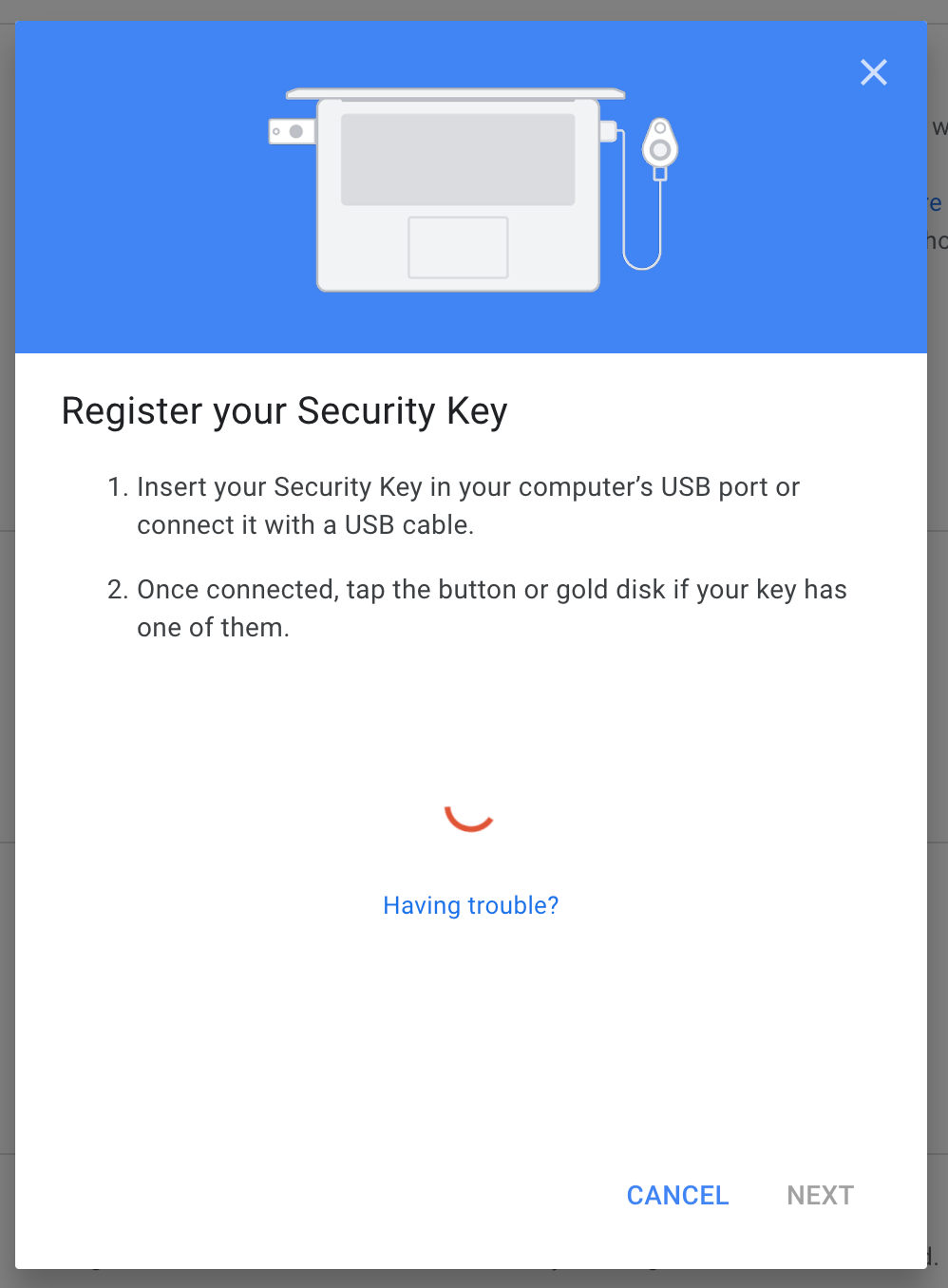
How this works is going to vary from app to app, but I'll use Google as an example. Follow the instruction for Google, and you'll find a link with instructions for adding your YubiKey to your Google account, which offers a link for adding your key.
You will be asked to plug in your device and press the button on it.
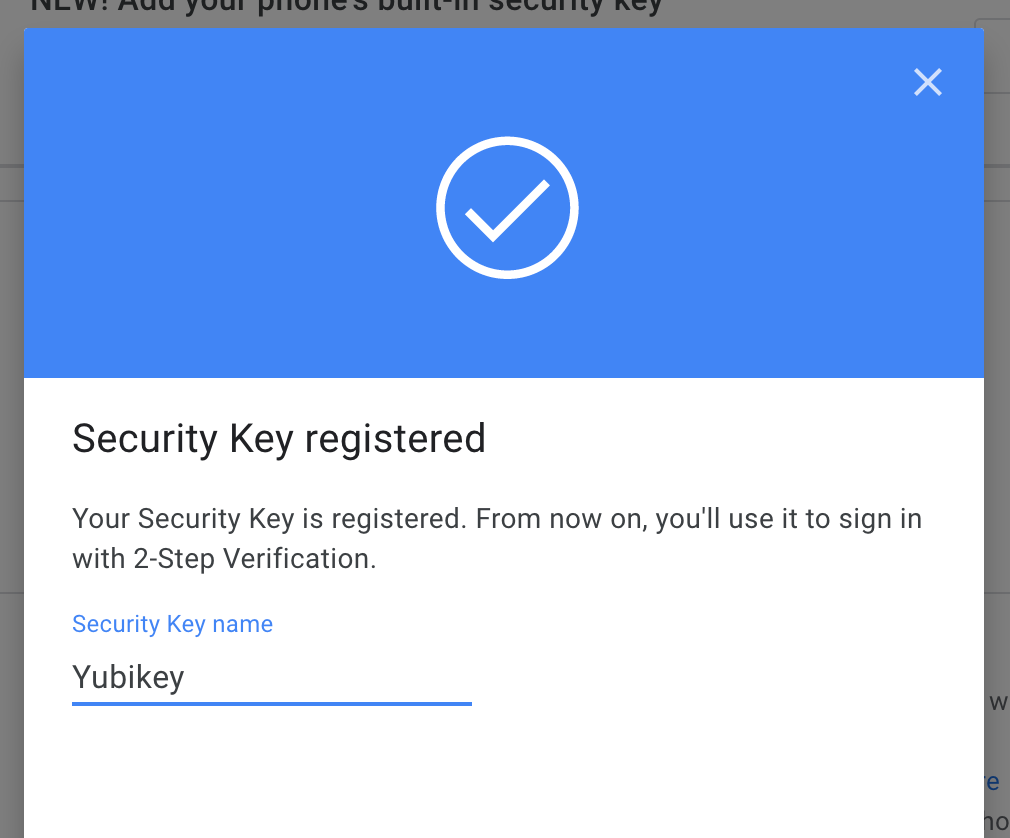
Do that. Your browser may ask for permission to access your key, but once you give that permission, you should get a confirmation that your key is set up. You can optionally give it a name, which is useful if you have multiple YubiKeys.
That's it. You can now use your YubiKey to log in to your Google account on any device. Repeat this process for every account you want to lock down in this way.
How do I stop accidentally triggering my YubiKey?
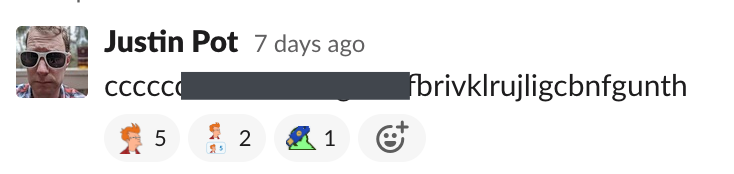
I own the YubiKey 5C Nano, which is a tiny USB-C dongle. I leave it plugged into my MacBook Pro, and it's surprisingly easy to trigger accidentally—particularly when picking up my laptop. It's not so much a button as it is a thin strip of metal that triggers when touched. When you touch it, it thinks you're trying to log in to something, which results in a secure code being entered in whatever text box you have open, and then the enter key being "pressed." The result, on Slack, looks like this:
These codes are generated by OTP, which is one of the protocols that your YubiKey uses to connect to servers. You could stop this from happening altogether by turning off OTP, but that might break your ability to log in to some services. I think, for most users, it's better to configure OTP to not trigger unless you hold the button for three seconds. This is a little complicated, but doable. YubiKey offers instructions for fixing this, but they're kind of hard to follow, so here's a summary.
To get started, download YubiKey manager on your computer. Install it, open the program, hover over Applications and click OTP.
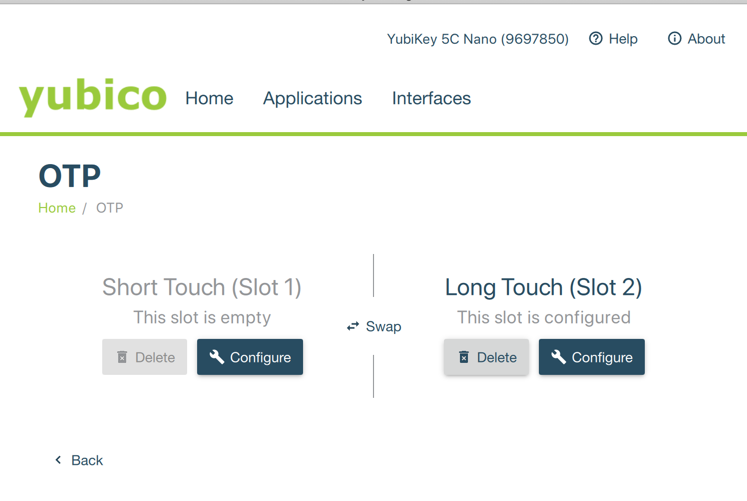
You should see two slots for OTP: the Short Touch, in Slot 1, and Long Touch, in Slot 2. Click the Swap button, so that OTP shows up in Slot 2. Like this:
In some cases it won't be this simple, but only if you've configured Slot 2 for some other purpose. You can read more on the YubiKey website if that's you.
Is accidentally triggering my YubiKey in a chat room really bad?
If you accidentally paste a code into something like Slack or a text editor, that's not a reason to immediately panic—it's not completely obvious who it belongs to or what it can be used to log in to (and, if you posted it on Slack, hopefully your coworkers aren't trying to hack you).
Having said that, there's always a chance a leaked 2FA code could enable a particularly creative hacker, so you don't want to make a habit out of this.
You're also not helpless if it happens. Every YubiKey code is unique, and becomes invalid every time you use the device to log in to something. You can manually invalidate codes, if you're worried. Just head to this website and paste the leaked code there.
At Zapier people accidentally post YubiKey codes on Slack…a lot. It's an internal meme at this point. It's funny, and probably harmless, but our security team set up an automated system to invalidate all such codes just in case. You can set it up if you want—click here to get started.
Can I use one YubiKey with multiple devices?
Yes! Just plug your YubiKey into any computer and log in the way you normally would. That's really it—you'll be able to log in to all of your accounts, same as before. You can use your YubiKey to log in on as many devices as you want, so long as there's a slot for it. This is nice if you own multiple devices, and also nice when you get a new computer.
What if I lose my YubiKey?
It's not great. Without your YubiKey you probably won't be able to log in. But there are a few things you can do to reduce the risk.
Most services that support 2FA (including YubiKey) allow you to create backup codes. Make sure you do this, and that you keep the codes somewhere secure—ideally offline. Consider printing them and putting them in a lockbox, if you can.
You could also add some other kind of 2FA to any service you set up with your YubiKey, as a fallback. This could be app-based verification, or you could buy a second YubiKey, add it as an option for all of your services, then store it somewhere safe (a different lockbox than the one your backup codes are in, maybe?).
If you don't have backup codes or a second 2FA method, and have already lost your YubiKey, you're not necessarily out of luck. Most services that offer 2FA have some kind of verification process for logging in after losing your credentials, but be warned: it's going to take a while, and it's going to be a lot of trouble. It's far better to be prepared, so make sure you have backup codes somewhere secure or a second 2FA method set up.
Also: make sure to remove your lost YubiKey as a 2FA method after you regain access to your account. Odds are whoever finds your YubiKey won't know which accounts it provides access to, but better safe than sorry.
To clarify: your Yubikey doesn't store identifiable usernames and does not store any of your passwords. Anyone who finds your YubiKey would have absolutely no way of knowing which accounts it can log in to. This changes a little if the person who "finds" it knows it's yours—say because they stole it from your house or office. But anyone who finds a YubiKey on the street, or in an airport, won't be able to figure out whose key it is.
The YubiKey seems intimidating, but it doesn't have to be. Set up your apps to use it, and you'll find that it's actually easier than other forms of two-factor authentication. Take it from someone who put it off for a long time—it's worth it.
Photo by Andre A. Xavier on Unsplash.