Improve Article
Save Article
Like Article
- Last Updated :08 Jul, 2022
Improve Article
Save Article
Like Article
Privacy Enhanced Mail (PEM) is an email security standard to provide secure electronic mail communication over the internet. Security of email messages has become extremely important nowadays. In order to deal with the security issues of emails the internet architecture board has adopted it.
The PEM mainly provides the following services –
- Confidentiality –
Confidentiality refers to the act of preventing unauthorized access to the information hence protecting it. The confidentiality is obtained in PEM by encrypting the messages by using various standard algorithms such as Data Encryption Standard (DES). DES in cipher block chaining mode is being currently used by PEM. - Integrity –
Data integrity refers to the consistency of data through out its life cycle. This is obtained by using a unique concept called as message digest where message digest is a hash function which converts the message into an image called digest on taking the message as input. PEM uses RSA encryption, MD2 and MD5 hash functions to generate the digests. An octet value is generated from the hash functions which is then encrypted which is then run against the message digest by the receiver assured of the integrity of the message that is transmitted.
Working of PEM :
The PEM works basically in 4 main steps.
- Canonical Conversion –
This step involves the conversion of the message into a standard format that is independent of the computer architecture and the operating system of the sender and the receiver. If the sender and receiver has different computer architecture or operating system. It may lead to generation of different message digest due to difference in their interpretation because of syntactical difference from one operating system to an other. - Digital Signature –
In this step, the digital signature is generated by encrypting the message digest of an email message with the sender’s private key.
- Encryption –
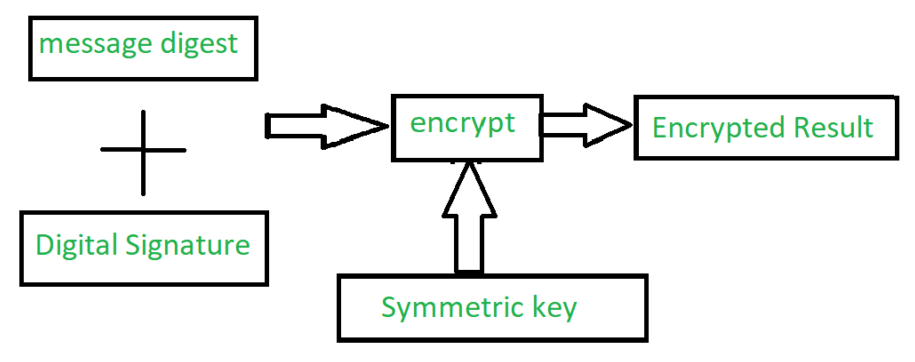
The encrypted message is generated by encrypting the original message and digital signature together along with the symmetric key as shown in the figure below.This step is very crucial in order to obtain the confidentiality.
- Base-64 Encoding –
This is the last step where the binary output is transformed into character output. The binary output which is 24 bits is divided into 4 equal sets and mapped with the 8 bit character output generating a decimal code. Now PEM uses a separate map table and each number from the code generated is mapped with its corresponding value from the mapping table and binary equivalent corresponding to the 8 bit ASCII of the character is written.
My Personal Notesarrow_drop_up
Like Article
Save Article